 ← ↑
← ↑  →GTALUG: Short Talks on Crypto
→GTALUG: Short Talks on CryptoTor, The Onion Router
Tuesday, 11 November 2014
at GTALUG: Greater Toronto Area Linux Users Group
by
Bob Jonkman of SOBAC Microcomputer Services
 ← ↑
← ↑  →About Bob Jonkman
→About Bob Jonkman
- System Administrator, Project Manager, Computer Course Instructor
- Free Software enthusiast, Social Justice activist
- Owner of

- Not a Mathematician, Cryptographer, Cryptologist, Cryptozoologist
 ← ↑
← ↑  →The Problem we're trying to solve:
→The Problem we're trying to solve:Being Anonymous on the Internet
- Prevent your ISP / Employer / Library from knowing what Web sites you visit
- Prevent the Web sites you visit from knowing your origin
 ← ↑
← ↑  →Not the Problem we're trying to solve:
→Not the Problem we're trying to solve: - Keeping your data transmission secure (TLS data encryption)
- Keeping your data storage secure (File and Disk encryption)
- Proving your identity (N-factor authentication)
- Verifying the Web site (Certificates)
Maybe the problem we're trying to solve:
- Maintaining your personal privacy (identity spoofing, anti-surveillance legislation)
 ← ↑
← ↑  →Target audience for this presentation
→Target audience for this presentation- Regular folks who want to preserve their privacy and anonymity
Not the target audience for this presentation:
- Web site operators who need Hidden Services
- Exit Node Operators
- People providing Privacy/Anonymity services to others
 ← ↑
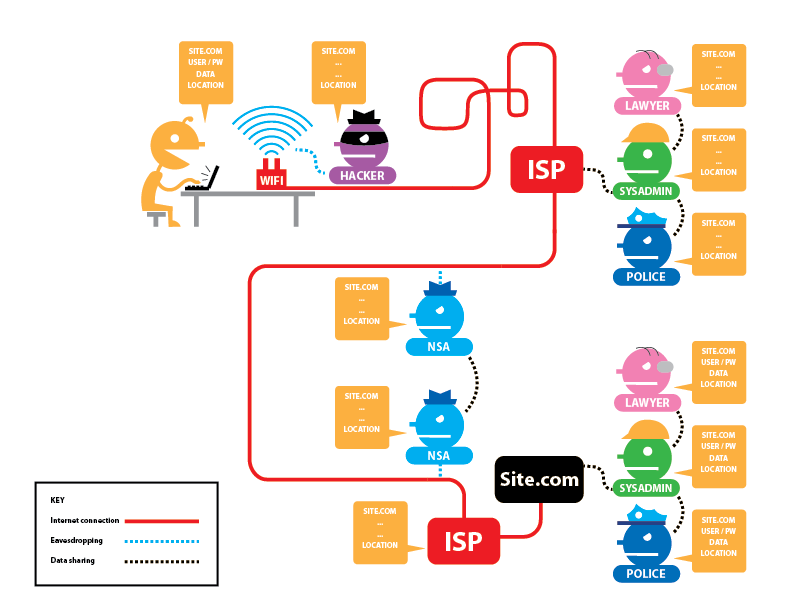
← ↑  →Tor is The Onion Router
→Tor is The Onion RouterHow it works:
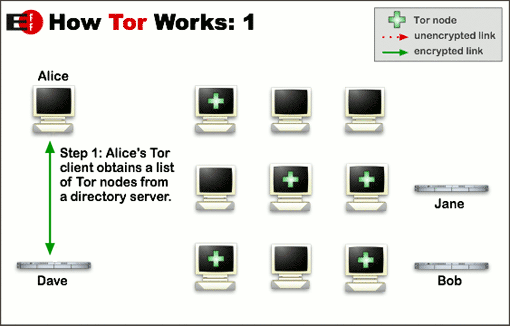
From Tor Project: Overview by the Tor Project, used under a
 CC BY 3.0 license
CC BY 3.0 license
 ← ↑
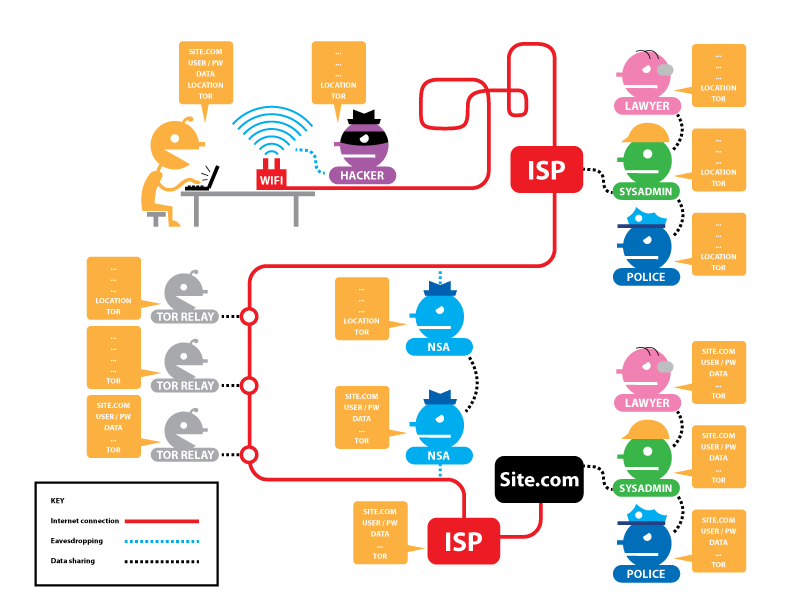
← ↑  →Tor is The Onion Router
→Tor is The Onion RouterHow it works:
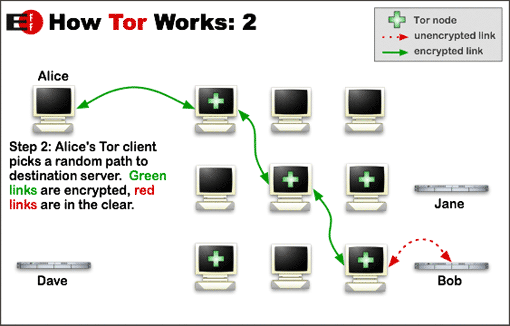
From Tor Project: Overview by the Tor Project, used under a
 CC BY 3.0 license
CC BY 3.0 license
 ← ↑
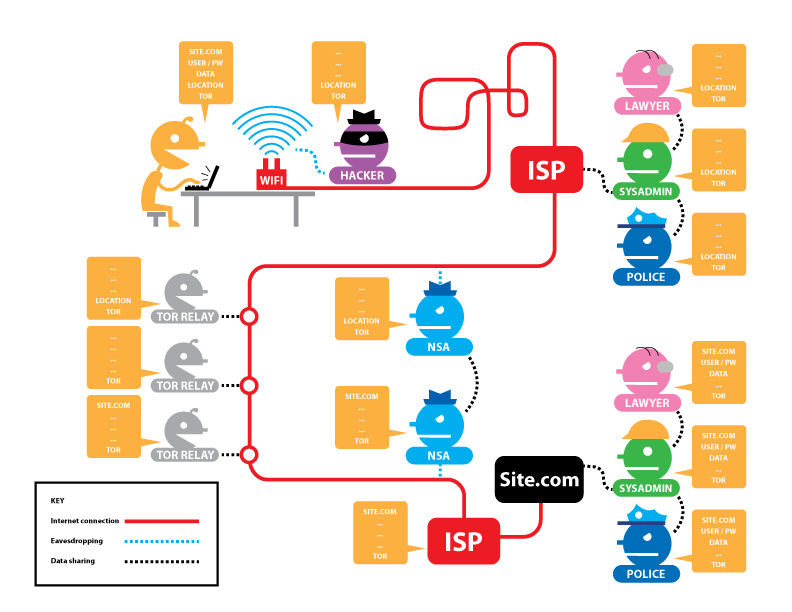
← ↑  →Tor is The Onion Router
→Tor is The Onion RouterHow it works:
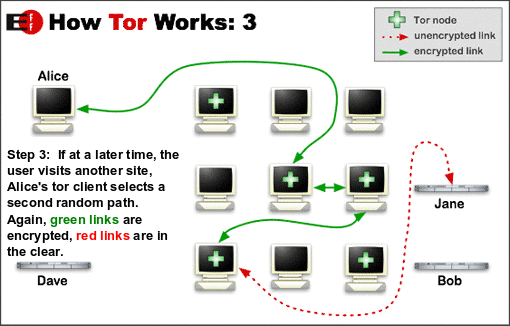
From Tor Project: Overview by the Tor Project, used under a
 CC BY 3.0 license
CC BY 3.0 license
 ← ↑
← ↑  →Best Practices
→Best PracticesBoot a clean, uncompromised computer
- An unknown computer already turned on may be running code to circumvent Tor
- Use Portable Tor or TOAST on computers you don't own
- Even better, use the portable operating system Tails on computers you don't own
 ← ↑
← ↑  →Best Practices
→Best PracticesBrowse only encrypted Web sites with https://
- Compromised exit nodes can see all unencrypted traffic
- Check certificates to make sure the SSL Certificate Authority is correct
 ← ↑
← ↑  →Best Practices
→Best Practices- No Tor, No HTTPS
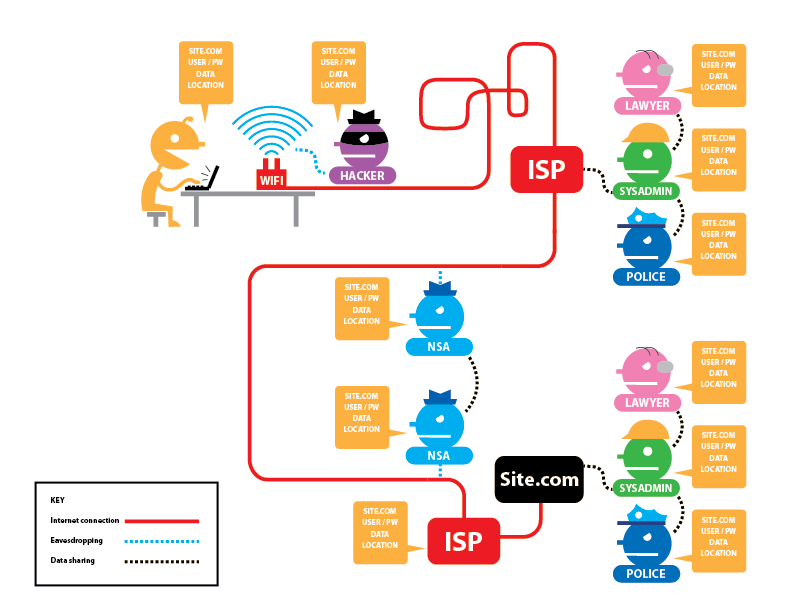
From Tor and HTTPS by the Electronic Frontier Foundation, used under a
 CC BY 3.0 license
CC BY 3.0 license
 ← ↑
← ↑  →Best Practices
→Best Practices- No Tor, HTTPS
From Tor and HTTPS by the Electronic Frontier Foundation, used under a
 CC BY 3.0 license
CC BY 3.0 license
 ← ↑
← ↑  →Best Practices
→Best Practices- Tor, No HTTPS
From Tor and HTTPS by the Electronic Frontier Foundation, used under a
 CC BY 3.0 license
CC BY 3.0 license
 ← ↑
← ↑  →Best Practices
→Best Practices- Tor, HTTPS
From Tor and HTTPS by the Electronic Frontier Foundation, used under a
 CC BY 3.0 license
CC BY 3.0 license
 ← ↑
← ↑  →Best Practices
→Best PracticesUse the Tor Browser Bundle
- Tor Browser is an Extended Support Release of Firefox (24.8.1esr), especially hardened against data leakage
- Tor Browser has specific Add-ons NoScript and HTTPS Everywhere to provide additional protection
 ← ↑
← ↑  →Best Practices
→Best PracticesUse only the software supplied with the Tor Browser Bundle
- Other Add-ons may be compromised to circumvent Tor
- Add-ons are written for an environment not designed for secure computing: XSS and XSRF
- Applications leak data (Ad tracking, DNS requests, OS calls)
 ← ↑
← ↑  →Best Practices
→Best PracticesDon't use Bittorrent
- Bittorrent enables peer-to-peer filesharing; P2P is the opposite of Onion Routing — your IP address is in every Bittorrent packet, tracker, Distributed Hash Table
- Bittorrent has far greater bandwidth requirements than the Tor network can deliver
 ← ↑
← ↑  →Other Considerations
→Other Considerations-
- Tor can be slow and laggy; browsing is painful, video and conferencing almost impossible
- Many sites ban traffic from Tor Exit Nodes
- Using Tor may harm your reputation
 ← ↑
← ↑  →Legal Considerations
→Legal Considerations-
IANAL
I Am Not A Lawyer
- Don't do illegal things!
- Merely using Tor will cast suspicion on your behaviour
- If you've done nothing wrong you have nothing to fear
- Corollary: What are you hiding if you're not doing anything wrong?
- Running a Tor Exit Node may allow others to use your computer to do illegal things
 ← ↑
← ↑  →Tor Failure Modes
→Tor Failure Modes-
- Many Tor Exit Node operators are the very people you're trying to be anonymous from: RCMP, CSIS, FBI, CRA
- Traffic Analysis works! — correlation of local traffic with Tor traffic can identify Tor users (Harvard University Exam Bomb Scare)
- OpSec is Hard! Traces of your activities while using Tor can reveal your identity (Tor and the Silk Road takedown, Dread Pirate Sunk By Leaky CAPTCHA)
- Infiltration Works! Silk Road 2 operator hired an undercover Homeland Security agent as a Web designer (Feds Seize Silk Road 2 in Major Dark Web Drug Bust)
- Tin Foil Hattery: Tor was designed as a US Defense Department project; Tor developers are US Government contractors
 ← ↑
← ↑  →Tor Downloads
→Tor Downloads-
- Official site: The Tor Project
- Software available for:
- Linux (32 bit)
- Linux (64 bit)
- Android: Orbot
- Windows (32 bit)
- Mac OSX (32 bit)
 ← ↑
← ↑  →Tor, The Onion Router
→Tor, The Onion Router-
Bob Jonkman
- E-mail: bjonkman@sobac.com
- !Fediverse: http://sn.jonkman.ca/bobjonkman
- Twitter: @BobJonkman
- Blog: http://bob.jonkman.ca/blogs
- This presentation: http://sobac.com/gtalug
Unless otherwise noted, all material is Copyright © 2014 by Bob Jonkman and SOBAC Microcomputer Services, and released under a
 CC BY 4.0 license
CC BY 4.0 license