Encrypting E-mail with GnuPG, Thunderbird and Enigmail
Revision as of 21:09, 25 November 2013 by BobJonkman (talk | contribs) (→Resources: Added Crypto Nut comic)
On Monday, 2 December 2013 I'm giving a presentation at KWLUG on Encrypting E-mail with GnuPG, Thunderbird and Enigmail which will be followed by a Formal Keysigning.
I'm using this page to develop my presentation notes. If you have comments, criticisms, or suggestions please put them on the Talk page.
--Bob.
I've started to convert this page to presentation slides BobJonkman 19:52, 19 November 2013 (UTC)
Contents
Intro to Crypto
Why use Encrypted E-mail?
- Security
- Your mail cannot be read by a Man In The Middle (MITM)
- Authenticity (Integrity)
- Signed mail cannot be modified in transit, accidentally by mis-configured servers, or maliciously by MITM
- Non-repudiability
- Signed mail can only come from the sender
Why NOT use Encrypted E-mail?
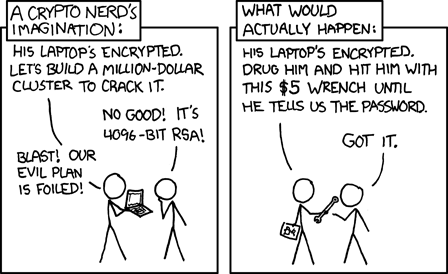
Rubber Hose Cryptography (using a $5 wrench). http://xkcd.com/538
- Need the other party to use the same encryption
- Locked-in format
- Lose your secret key, lose your mail
- Need to keep revoked keys to read old mail
- If your key is compromised, all your old mail is compromised (no forward secrecy)
- Non-repudiability
- Politicians? CEOs?
- Rubber Hose Cryptography (or $5 Wrench Cryptography)
- It's hard!
- and looks geeky...
Date: Mon, 25 Nov 2013 18:27:22 -0500 From: Crypto Guy <cryptoguy@sobac.com> Subject: Hello! Hello World! |
vs. | Date: Mon, 25 Nov 2013 18:27:22 -0500 From: Crypto Guy <cryptoguy@sobac.com> Subject: Hello! -----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 Hello World! -----BEGIN PGP SIGNATURE----- Version: GnuPG v1.4.14 (GNU/Linux) Comment: Using GnuPG with Thunderbird - http://www.enigmail.net/ iQEcBAEBAgAGBQJSk9zaAAoJENrSxFs55fZVAAgIAK2BKzV/qUTXCu0gEWJq2U3z mZ6nsfzjs8aXJe8CT/c7kr7HSgSV57kvukIbvcUP5sCGwpIfwK04qA0Af4J9jXp7 Wq1/k0wjA1WzhCWUEEjdBs/05bAbQ78ulTbhFlII2ywLgH6BYxgjceZa9abgF8Di xHkRWEAI6q+scoEhi0rCGlCX3UX/pkiZ1GlaxxxMBu1J5DbFaAJZ1MiPUDOLQN9w 5LzIqi4rKTtnCQo6G3WWRg5HvPMHHmUJoaZfZpnPrszf4ttG0vrFLxJKUqZszDyr V5Lx/IjKAZBwoRRjfpRZILFHWoveaw5MG8487jM76W7LiVTEsX2AFGI3R6uy+KA= =0p58 -----END PGP SIGNATURE----- |
Crypto Theory
Symmetric Key Encryption
- Substitution cipher, Caesar cipher
- Key = -1
- Encrypt: IBM -1> HAL
- Decrypt: Khmtw Trdq Fqnto +1> Linux User Group
- Key = 13 (ROT13)
- Encrypt: Linux User Group +13> Yvahk Hfre Tebhc
- Decrypt: Yvahk Hfre Tebhc +13> Linux User Group
- Key = -1
- Need a secure way to share key
Public/Private Key Encryption
The Math
- Based on One-way function: Easy to do, hard to reverse
- 59 x 61 = ????
- 59 x 61 = 3599
- 3551 = ?? x ??
- 3551 = 53 x 67
- 59 x 61 = ????
The Practice
- Generate a keypair
- Add e-mail and identity information as you see fit
- Public Key, Private (Secret) Key
- Anything encrypted by one key is decrypted by the other
- Encrypt: Hello World +P> |-|3110 '//0|21|)
- Decrypt: |-|3110 '//0|21|) +S> Hello World
- Encrypt: Linux Is Cool +S> 1!/\/|_|>< !5 (001
- Decrypt: 1!/\/|_|>< !5 (001 +P> Linux Is Cool
- Keep your Secret Key secret!
- But you can distribute your Public Key widely
- Upload your Public Key to keyservers
- Send your Public Key by e-mail
- Use a Public Key to encrypt a message
- Only that person's Secret Key can decrypt it
- You can only encrypt a message to someone whose Public Key you have
- Use your Secret Key to sign (encrypt) a message
- Anyone can use your Public Key to verify (decrypt) the signature, which only you could have created
- You can sign messages for everyone!
- But only people who have your Public Key can verify the signature
- Shows others that encryption is not such a weird thing
- If I download your Public Key, how do I know it's really yours?
- Keysigning!
- You tell me what your Key Fingerprint is.
- I verify that's the same Key Fingerprint on the Public Key I download
- If I believe that's your Public Key, I sign it.
- Web of Trust
- Your Public Key has been signed by others
- I already trust their Public Keys, some of that trust transfers to your Public Key
- Keysigning!
Demonstration
Install Enigmail
Use Wizard
Generate keypair
If your Key Fingerprint is 04F7 742B 8F54 C40A E115 26C2 B912 89B0 D2CC E5EA
- Then your Long KeyID is 0xB91289B0D2CCE5EA
- And your Short KeyID is 0xD2CCE5EA
- Short KeyID is unique to about 1 in 10 billion (2^32)
- Long KeyID is unique to about in 10^20 (2^64)
- Key Fingerprint is unique to about 10^48 (2^160)
- Number of atoms in the universe is about 10^80
Configure Enigmail
Generally, use the defaults.
- I chose DSA for my key because of patent restrictions in 1999
- Use PGP/MIME to hide signature blocks
- But displaying signature blocks may encourage others to use encryption
- Some mailing lists may remove PGP/MIME signature attachments
Retrieve a Public Key
- E-mail address is convenient, but may return multiple keys
- KeyID search will return one key. Prefix KeyIDs with "0x"
Sending a Message
- OpenPGP ⇒ Default Composition Options ⇒ Signing/Encryption Options
- OpenPGP ⇒ Per-Recipient Options
Receiving a Message
How to use PGP to verify an e-mail is authentic

from http://xkcd.com/1181
Fortunately, Enigmail checks a little more thoroughly!
Keysigning with Enigmail
- OpenPGP ⇒ Key Management ⇒ Edit ⇒ Sign Key
Resources

What do to with encrypted mail and who to do it with http://xkcd.com/1269
- KWCrypto Interest Group: http://sobac.com/kwcrypto
- PGP-Basics mailing list: http://groups.yahoo.com/neo/groups/PGP-Basics/info
- KWLUG: http://kwlug.org
- Bob Jonkman
- E-mail: mailto:bjonkman@sobac.com
- Microblog: @bobjonkman@sn.jonkman.ca or http://sn.jonkman.ca/bobjonkman
- XMPP: xmpp:bjonkman@sobac.com
