Encrypting E-mail with GnuPG, Thunderbird and Enigmail
On Monday, 2 December 2013 I'm giving a presentation at KWLUG on Encrypting E-mail with GnuPG, Thunderbird and Enigmail which will be followed by a Formal Keysigning.
I'm using this page to develop my presentation notes. If you have comments, criticisms, or suggestions please put them on the Talk page.
--Bob.
I've started to convert this page to presentation slides BobJonkman 19:52, 19 November 2013 (UTC)
Contents
Intro to Crypto
Why use Encrypted E-mail?
- Security
- Encrypted mail cannot be read by a Man In The Middle (MITM)
- Authenticity (Integrity)
- Signed mail cannot be modified in transit, accidentally by mis-configured servers, or maliciously by MITM
- Non-repudiability
- Signed mail can only come from the sender
Why NOT use Encrypted E-mail?
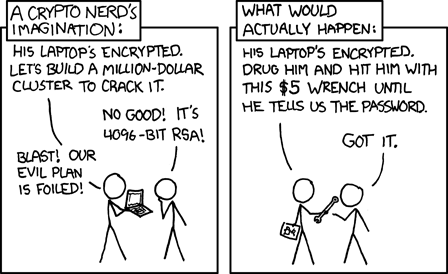
- Need the other party to use the same encryption
- Locked-in format
- Lose your secret key, lose your mail
- Need to keep revoked keys to read old mail
- If your key is compromised, all your old mail is compromised (no forward secrecy)
- Non-repudiability
- Politicians? CEOs?
- Rubber Hose Cryptanalysis (or $5 Wrench Cryptanalysis)
- It's hard!
- and looks geeky...
Unencrypted, unsigned message
Date: Mon, 25 Nov 2013 18:27:22 -0500 From: Crypto Guy <cryptoguy@sobac.com> To: Crypto Guy <cryptoguy@sobac.com> Subject: Hello! Hello World!
Unencrypted, signed message
Date: Mon, 25 Nov 2013 18:27:22 -0500 From: Crypto Guy <cryptoguy@sobac.com> To: Crypto Guy <cryptoguy@sobac.com> Subject: Hello! -----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 Hello World! -----BEGIN PGP SIGNATURE----- Version: GnuPG v1.4.14 (GNU/Linux) Comment: Using GnuPG with Thunderbird - http://www.enigmail.net/ iQEcBAEBAgAGBQJSk9zaAAoJENrSxFs55fZVAAgIAK2BKzV/qUTXCu0gEWJq2U3z mZ6nsfzjs8aXJe8CT/c7kr7HSgSV57kvukIbvcUP5sCGwpIfwK04qA0Af4J9jXp7 Wq1/k0wjA1WzhCWUEEjdBs/05bAbQ78ulTbhFlII2ywLgH6BYxgjceZa9abgF8Di xHkRWEAI6q+scoEhi0rCGlCX3UX/pkiZ1GlaxxxMBu1J5DbFaAJZ1MiPUDOLQN9w 5LzIqi4rKTtnCQo6G3WWRg5HvPMHHmUJoaZfZpnPrszf4ttG0vrFLxJKUqZszDyr V5Lx/IjKAZBwoRRjfpRZILFHWoveaw5MG8487jM76W7LiVTEsX2AFGI3R6uy+KA= =0p58 -----END PGP SIGNATURE-----
Encrypted, signed message
Date: Date: Mon, 25 Nov 2013 18:27:22 -0500 From: Crypto Guy <cryptoguy@sobac.com> To: Crypto Guy <cryptoguy@sobac.com> Subject: Hello! -----BEGIN PGP MESSAGE----- Charset: ISO-8859-1 Version: GnuPG v1.4.14 (GNU/Linux) Comment: Using GnuPG with Thunderbird - http://www.enigmail.net/ hQEMA7bHREkg/1GxAQf/dmPoG27m33QGlUEZ0F9rlndQJFgeAyPBpXVEV2uCgaGw rCzeBOkcE7FMmo2MjiozS64QaynPAGuHYoKwRIYS06Aa3ll2FwFO4O2tGiC1jsGQ EUgjIE8h4iqIG4D5uzsv/iQ14QWJm4vaACxLCEtSaIRYcNB6Kxvy0phydltc3cp1 Ri1OlYPV799yiT7bcdT3ntTew5UF853mUrEIPt3NRfEDrC/m8ScTCT9SD2VRzlfA qMviBt20XgApQscLBOWCAHv+1u2eUQ8AM3OsAZ/K4mw+s/jcWNNqLG9DRrrHJzMK YXiZtLuE02eqpXjxrgfKmUloWAu7p9uQHMRwJjIy89LAugFdmW8HY1eZbpu7kUQU 9PvGydWd0QUPjkG7CXEeh63hmmbJgmJdjqOVjDuXhuHI1xU9+psmLPEszAY1TP9f V4WR7SAIIVtE5r2S3YRwgyXWsPF+VgesBiUtQ7mroSGeVJ6GRR/rn0IdnLabrJsb WXiCAtNajDx/x1QGcxFDIQjNsnqvzraSHwcpX6XelRCIz3jyS3SKDdR0T/x5YkmA mkmXDZlLUntyjbJjZF0LmB96PTAi8JT/OG4QCxTsPMIpkLJZOcQ4SnHsaxfVgLqg gOt5bxT9ybGt17xrw/j/mKpcq9cbyXFVJoRr73OVE8Wg2IYBye4TPu/HfXIGUh70 s4dE1Jc+iqdVLqJ2w3qGo4v8B2pg6bPLde7TT/7NrrvEWg0Zxlr+SFr+60xiyPGu 8eJHtQYSXe4OOc2FZev9mb0M2IIr0zpd7q5MvUqE+4b/VUtmadUFcExuUdaayS0P rgLVNx3285jGXzelaFB2/+Gzx/m7MMXsKMBX7Q== =jfdJ -----END PGP MESSAGE-----
Crypto Theory
Symmetric Key Encryption
- Substitution cipher, Caesar cipher
- Key = -1
- Encrypt: IBM ⇒ -1 = HAL
- Decrypt: Khmtw Trdq Fqnto ⇒ +1 = Linux User Group
- Key = 13 (ROT13)
- Encrypt: Linux User Group ⇒ +13 = Yvahk Hfre Tebhc
- Decrypt: Yvahk Hfre Tebhc ⇒ +13 = Linux User Group
- Key = -1
- Need a secure way to share key
Public/Private Key Encryption
The Math
Based on One-way function: Easy to do, hard to reverse
- 59 x 61 = ????
- 59 x 61 = 3599
- 3551 = ?? x ??
- 3551 = 53 x 67
The Theory
Generate a keypair
- Add name, e-mail and comment (doesn't have to be your real name or e-mail)
- Public Key, Private (Secret) Key
- Anything encrypted by one key is decrypted by the other
- Encrypt: Hello World ⇒ Public Key = |-|3110 '//0|21|)
- Decrypt: |-|3110 '//0|21|) ⇒ Secret Key = Hello World
- Encrypt: Linux Is Cool ⇒ Secret Key = 1!/\/|_|>< !5 (001
- Decrypt: 1!/\/|_|>< !5 (001 ⇒ Public Key = Linux Is Cool
In Practice
- GnuPG/PGP uses a symmetric key, not Public/Secret keys to encrypt a message
- Symmetric Key generated by Pseudo Random Number Generator (PRNG)
- Symmetric Key is encrypted with recipient's Public Key
- Bob encrypts a message to Alice
- GnuPG/PGP generates a random Symmetric Key
- Message ⇒ Symmetric Key = |\/|355463
- Symmetric Key ⇒ Alice's Public Key = 5`/|\/||\/|37|2!( |<3`/
- Bob sends |\/|355463 5`/|\/||\/|37|2!( |<3`/ to Alice
- Alice decrypts a message from Bob
- 5`/|\/||\/|37|2!( |<3`/ ⇒ Alice's Secret Key = Symmetric Key
- |\/|355463 ⇒ Symmetric Key = Message
- Bob signs a message
- Message ⇒ Hash = ABC
- ABC ⇒ Bob's Secret Key = 4|>(
- Alice checks Bob's signature
- 4|>( ⇒ Bob's Public Key = ABC
- Message ⇒ Hash = ABC
- Same result? Message is untampered!
Practical GnuPG/PGP
- Keep your Secret Key secret!
- But you can distribute your Public Key widely
- Upload your Public Key to keyservers
- Send your Public Key by e-mail
- Use a Public Key to encrypt a message
- Only that person's Secret Key can decrypt it
- You can only encrypt a message to someone whose Public Key you have
- Use your Secret Key to sign a message
- Anyone can use your Public Key to verify the signature
- You can sign messages for everyone!
- But only people who have your Public Key can verify the signature
- Shows others that encryption is not such a weird thing
- If I download your Public Key, how do I know it's really yours?
Keysigning!
- You tell me what your Key Fingerprint is.
- I verify that's the same Key Fingerprint on your Public Key I download
- If I believe that's your Public Key, I sign it.
- Alice's Public Key ⇒ Bob's Secret Key = 5!6|>0|>
- Alice's Public Key + 5!6|>0|> = Alice's Public Key5!6|>0|>
- Alice is popular: Alice's Public Key5!6|>0|>5!6(4|2015!6|\/|41(01|\/|
- Web of Trust
- Carol's Public Key has been signed by others
- Carol's Public Key5!641!(35!6|\/|41(01|\/|
- 5!641!(3 ⇒ Alice's Public Key = Carol's Public Key
- I already trust Alice's Public Key, some of that trust transfers to Carol's Public Key
Demonstration
Install Enigmail
Use Wizard
Generate keypair
If your Key Fingerprint is 04F7 742B 8F54 C40A E115 26C2 B912 89B0 D2CC E5EA
- Then your Long KeyID is 0xB91289B0D2CCE5EA
- And your Short KeyID is 0xD2CCE5EA
- Short KeyID is unique to about 1 in 10 billion (2^32)
- Long KeyID is unique to about in 10^20 (2^64)
- Key Fingerprint is unique to about 10^48 (2^160)
- Number of atoms in the universe is about 10^80
Configure Enigmail
Generally, use the defaults.
- I chose DSA for my key because of patent restrictions in 1999
- Use PGP/MIME to hide signature blocks
- But displaying signature blocks may encourage others to use encryption
- Some mailing lists may remove PGP/MIME signature attachments
Retrieve a Public Key
- E-mail address is convenient, but may return multiple keys
- KeyID search will return one key. Prefix KeyIDs with "0x"
Sending a Message
- OpenPGP → Default Composition Options → Signing/Encryption Options
- OpenPGP → Per-Recipient Options
Receiving a Message
How to use PGP to verify an e-mail is authentic

from http://xkcd.com/1181
Fortunately, Enigmail checks a little more thoroughly!
Keysigning with Enigmail
- OpenPGP → Key Management → Edit → Sign Key
Resources

Other tools
- Evolution — Built-in support for GnuPG
- Claws — Plugins PGP/Core, PGP/Inline, PGP/MIME
- KMail — use gnupg2 package
- Mutt — Built-in support
- GMail — Use Chromium and plugin cr-gpg
- Other Webmail (Yahoo!, Hotmail, &c.) — Cut'n'paste with Firefox plugin WebPG (doesn't work for me)
Support
- KWCrypto Interest Group: http://sobac.com/kwcrypto
- PGP-Basics mailing list: http://groups.yahoo.com/neo/groups/PGP-Basics/info
- KWLUG: http://kwlug.org
This presentation is online at http://sobac.com/KWCrypto/kwlug-2013-12-02/
Bob Jonkman
- E-mail: mailto:bjonkman@sobac.com
- Microblog: @bobjonkman@sn.jonkman.ca or http://sn.jonkman.ca/bobjonkman
- XMPP: xmpp:bjonkman@sobac.com
Thanx to Randall Monroe for releasing XCKD comics under a CC-BY-NC 2.5 license!
The Cryptoparty keypair logo from the Cryptoparty Artwork repository on GitHub is available in the Public Domain.
This rest of this presentation is © 2013 by Bob Jonkman and released under a CC-BY 4.0 license.
